Kyocera Intelligence is a top Baltimore IT support company. When Keith Marchiano needed a new website for the IT Services division, he chose Ulistic.
 Baltimore IT Support Company Works With Ulistic
Baltimore IT Support Company Works With Ulistic
Kyocera Intelligence is a top Baltimore IT support company. When Keith Marchiano needed a new website for the IT Services division, he chose Ulistic.
 Spoofing & Hacking: What’s The Difference?
Spoofing & Hacking: What’s The Difference?
Most people know not to open email attachments from senders that they do not know. Unfortunately, it is not just attachments from strangers that you have to be on the lookout for. It happens quite often that people will get emails that seem to be from known senders that have malicious attachments, or that ask […]
 Google’s New Chrome Extension Gives Your Passwords a Checkup
Google’s New Chrome Extension Gives Your Passwords a Checkup
In early 2019, white-hat security expert Troy Hunt and other researchers shared a massive database of breached passwords and usernames. The stolen data constitutes 25 billion records and 845 gigabytes of stolen data. While many of the collected records are from previously reported thefts, there are new records there, too. It’s a clear indication of regularity, scope and potential damage […]
 4 Strategies For Super Strong Passwords
4 Strategies For Super Strong Passwords
Some days it seems like everything in our lives requires a password: banks, apps, debit and credit cards, online banking, business applications, healthcare accounts . . . the list is literally endless. Technology professionals recommend that you use a different and highly secure password for each site — but how is it even possible for […]
 How to Get the Most From Your Android Battery
How to Get the Most From Your Android Battery
Battery technology has come a long way in the past several decades. Today’s lithium-ion batteries are a pretty amazing feat of engineering, offering high capacity, low power leakage, and comparatively long life. That said, they aren’t perfect, and they don’t last forever. Getting the most use out of your phone’s battery requires a little effort […]
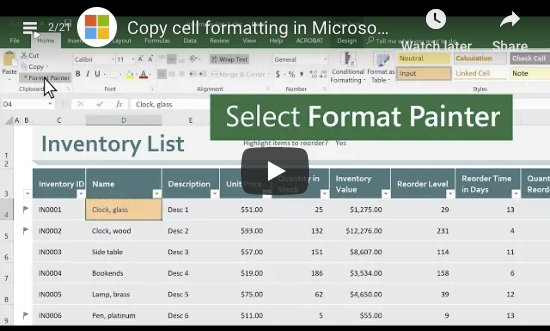 How to Copy Cell Formatting in Microsoft Excel
How to Copy Cell Formatting in Microsoft Excel
Excel is a powerful application, but because it can do so much it can be easy to miss certain features that could make your life much simpler. Today’s quick tech blog shows you one of these features. We’ll look at how to copy cell formatting in Microsoft Excel without disturbing the contents of the cells […]
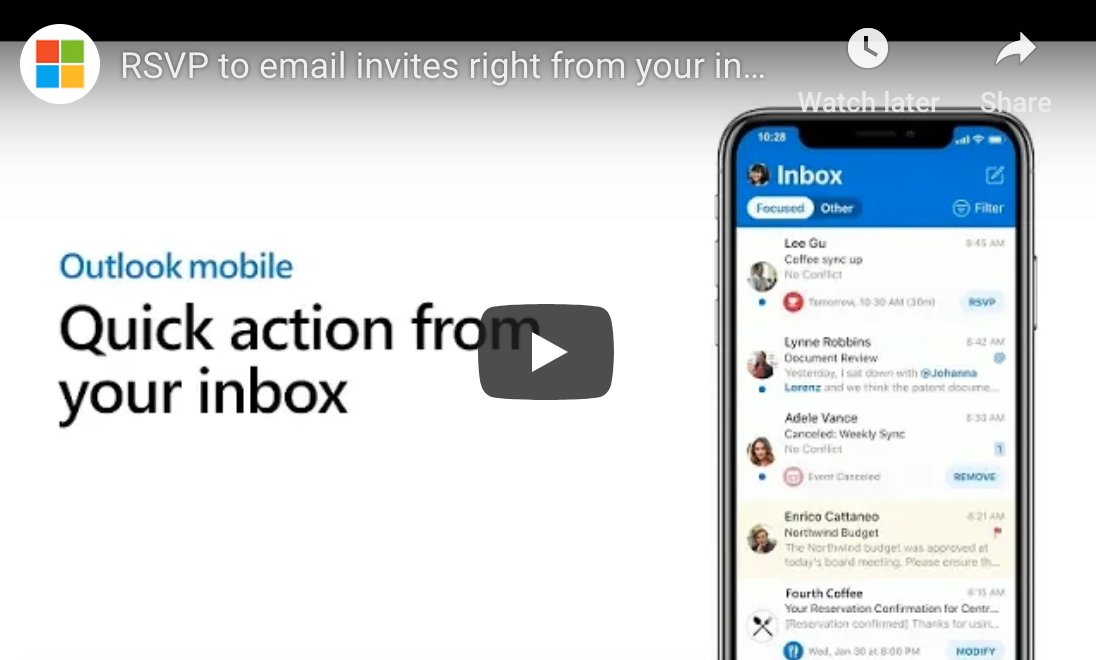 How to RSVP to Invites With Outlook Mobile
How to RSVP to Invites With Outlook Mobile
Outlook Mobile is a powerful mobile version of Microsoft’s popular Outlook application. Microsoft has provided users a standalone email app that’s packed with a real depth of features. Today we’re looking at how to quickly RSVP to meeting invites using Outlook Mobile. The best and quickest way to do this uses an Outlook Mobile feature […]
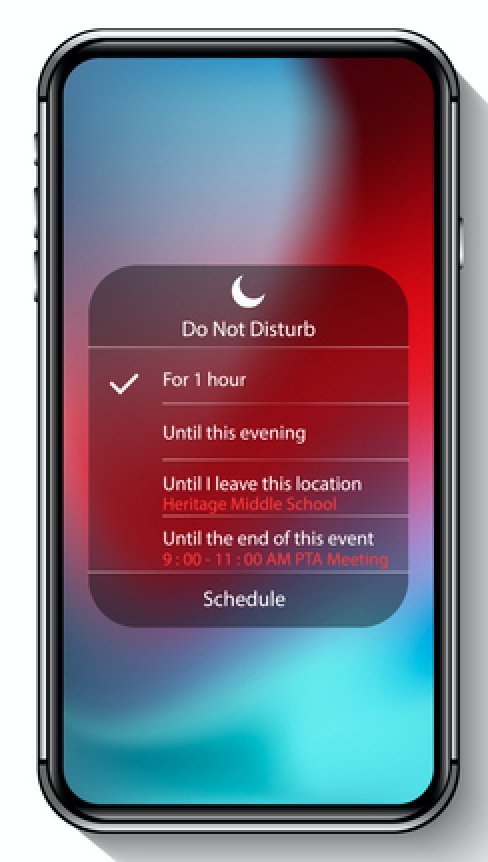 Enable Do Not Disturb on Your Android Device
Enable Do Not Disturb on Your Android Device
Do Not Disturb on Android can do more than you might expect. Here’s how to enable and customize Do Not Disturb on your Android device. Today’s quick tech blog explains how to enable Do Not Disturb on Android devices. We’ll also give a basic explanation of how to customize this feature, making it even […]
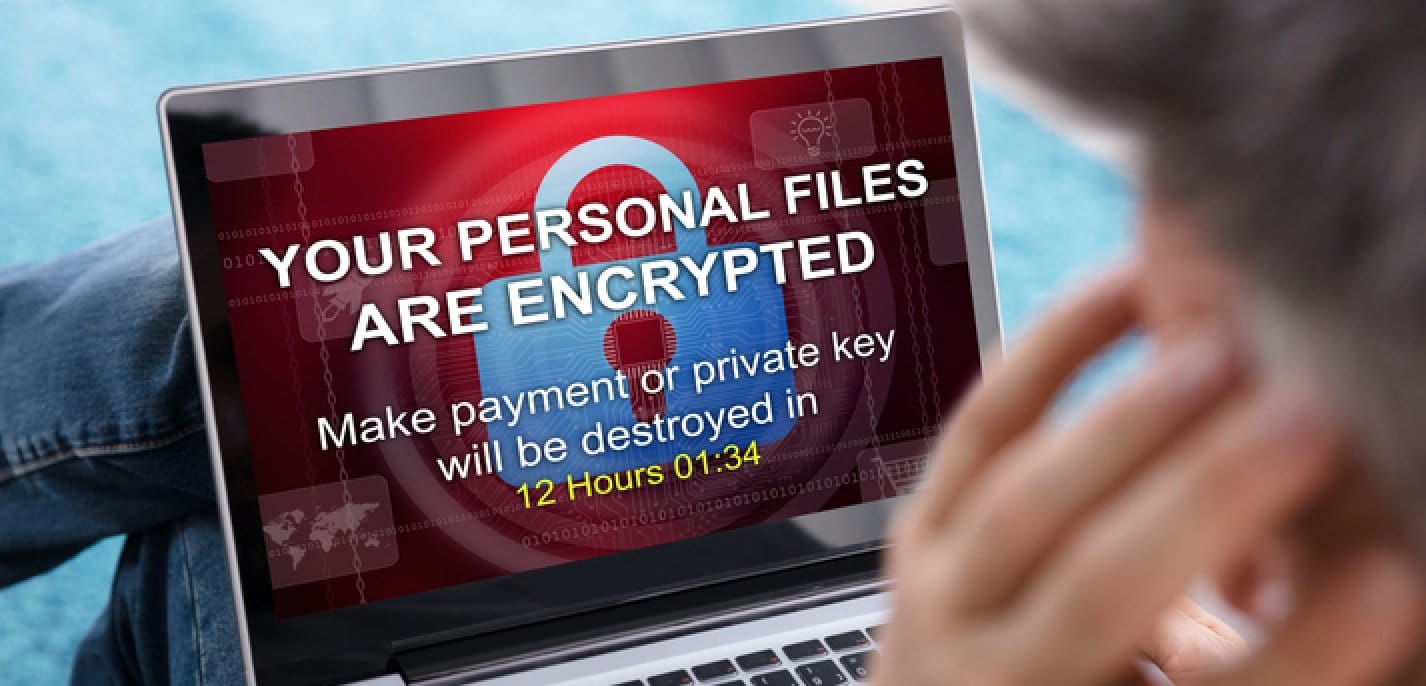 Most Small Businesses Pay The Ransom
Most Small Businesses Pay The Ransom
Are you willing to pay the piper when it comes to cyberattacks? Despite the growing number of cyberattacks on small- and medium-sized businesses, there is still a lack of awareness or proactive defense of the networks, computer systems, applications and devices being used. This inattention means it’s even easier for criminals to attack your business […]
 MSP Legal Corner: What Is A Master Services Agreement?
MSP Legal Corner: What Is A Master Services Agreement?
Learn what's included in a master services agreement, what you need to decide when building one and why it's important to protect your managed service provider.
Call Us: (855) 964-2608 | Privacy Policy